Work Completed By: Chris Jones
DRAFT
DESCRIPTION
In order to rationalise the way in which we handle identity information, while also providing the benefits that contextual access will give us, we need to move to a model for accessing our services that is more flexible than our current practice of dealing with identity in technology and information silos.
Identity theory is centralising around the idea of claims i.e. a piece of information about an individual that is in doubt and must therefore be proved. Using an identity model based around claims allows individual identities to hold many disparate roles which can relate to different organisations as part of a wider ID metasystem. The way in which these claims are asserted and proven can be handled by a variety of technical solutions and services.
Investigate how a claims-based identity model could be implemented to provide personalisation and role based security. Find examples of where such a model is already in use and evaluate its potential usefulness as part of WCC’s service oriented architecture.
DETAILS/LOCATION OF PRACTICAL DEMONSTRABLE OUTPUT
Details of where code, web pages etc can be found.
DESCRIPTION OF THE WORK CARRIED OUT
Describe how you approached this piece of work, any technologies, tools or techniques that you found useful or tried and discarded. Include any examples that you used for inspiration and any contacts you have made in carrying out the work.
On the surface this seems a large scope for such a small R&D project, so it was difficult to know exactly where to begin. I started by investigated the below areas to gain knowledge of what a claims-based identity model is, help define what’s involved and what technology can be used. With this knowledge I hope to gain a better understanding of how and whether this model can and should be incorporated within WCC’s service oriented architecture.
Geneva Framework
The Geneva Framework is used for building claims-based applications and services for ASP.NET applications. Features include:
- Security Token Services (STS)
- Federated authentication from ASP.NET applications
- Object Model that facilitates claims-based authorization form ASP.NET applications
The above definition was taken from the below URL, this webpage also gives a more in-depth look at what is a claims based system is and how the Geneva framework fits in.
http://msdn.microsoft.com/en-us/magazine/dd278426.aspx
After reading the above document it still seemed a little confusing, probably because of my lack of knowledge in this area so I decided to setup the Framework to try and get a better understanding. This involved setting up a VM with Windows Server 2008, installing Visual Studio, the Geneva Framework and IIS7. I followed the below blog, which seemed a very good source to get the Framework up and running.
Once all setup, the Framework provides you with a couple of examples to get started. I looked at the first one which I've documented below, A Simple Claims Aware Web Application.
The sample includes a Security Token Service (STS) and two web applications that show two different mechanisms (PassiveRedirectBasedClaimsAwareWebApp, WebControlBasedClaimsAwareWebApp) to obtaining the federated token.
1) PassiveRedirectBasedClaimsAwareWebApp
This web application illustrates the use of the passive-redirect feature of the WSFederationAuthenticationModule object available in the Geneva Framework. When a user browses this web site, the WSFederationAuthenticationModule checks to see if he or she is authenticated. If the user is not authenticated, the browser will redirect automatically to the STS web site.
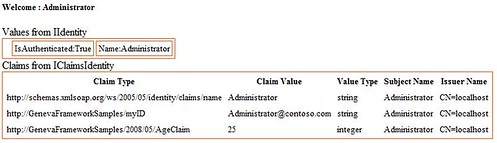
2) WebControlBasedClaimsAwareWebApp
This web application illustrates the use of the FederatedPassiveSignIn ASP.NET web control available in the Geneva Framework. When a user first browses this web site, he or she will see a page with a “Sign In” icon. Upon clicking this icon, the user’s browser will redirect to the STS web site.


Google App Engine: An OpenID consumer example
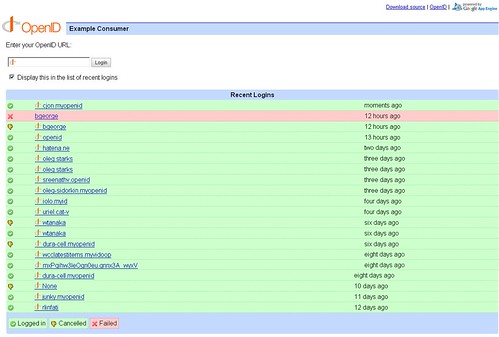
Within the Google App Sample code section there is a Python OpenID consumer application. This allows users to log into other OpenID providers, then displays their OpenID login. Also stores and displays the most recent logins.
First the below login screen is shown, here the user enter their login id.
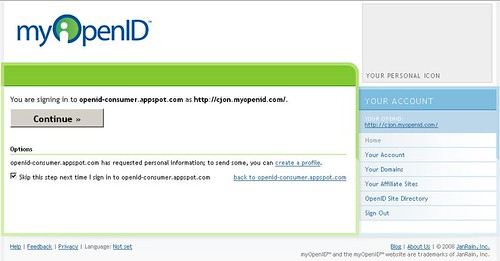
On pressing the Login button, the user is redirected to their OpenID provider to confirm where they are logging into and with what ID.
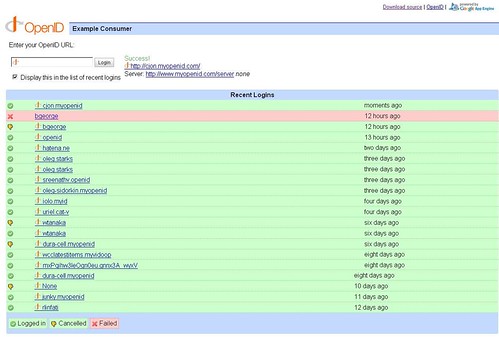
Pressing continue returns the user to the consumer application logged in with the chosen ID, see below:
A full demonstration of the code has been uploaded to this URL
http://openid-consumer.appspot.com
DotNetOpenId C# Library
Adds OpenID 2.0 Provider and Relying Party, OAuth Consumer and Service Provider, and InfoCard Selector support to your web site both programmatically and through convenient drop-in ASP.NET controls.
First the below login screen is shown, here the user enter your login id.
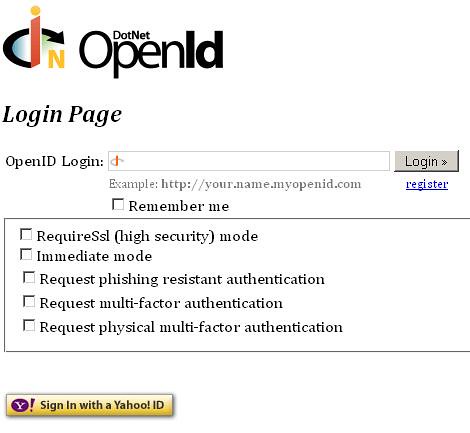
On pressing the Login button, the users are redirected to their OpenID provider to confirm where they are logging into and with what ID.

Pressing Continue returns the user to the consumer application logged in with their chosen ID, see below:

GovTrack example OpenID site
Allows users to use sign in with existing GovTrack accounts and OpenId accounts. Also Allows them to register a new GovTrack accounts, but recommends using OpenID instead.
Brings information such as email address across from my OpenId account, this can be changed within GovTrack’s account settings. So it seems info from my OpenID is initially brought across to form the bases of my GovTrack’s account. Additional within the GovTrack’s account you can even change to another OpenID.
PROJECT OUTCOME
Describe the degree to which the work was successful in addressing the project description. Include reasons why or why not.
Identity 2.0 is an anticipated revolution where authentication on the internet becomes more user-centric. This means that instead of each website acting in identity silo's, users will be able to use the same identity from one site to another. This can currently be easily defined in the physical world with say a Driving Licence, where first it proves you can driver, but it can also be used to prove your age.
I couldn’t find any online banks or government sites that currently use OpenId. So it maybe a bit risky to become such an early adopter. However I believe its only at matter of time for this idea to fully establish itself for general users. This is based on the following reasons:
- Firstly most major email provides such as Google, Hotmail and Yahoo have already turn email accounts into OpenId accounts as well.
- Secondly for low risk authentication for example wiki's/blogs etc, users just want to get in and will therefore take whatever the easiest method is for registration. Therefore when users begin to realise they already have an OpenId's, they will begin to user this method, firstly because it will be easier to register as user users will not have to fill out any major details and secondly they will not have to remember so many passwords. Also with Microsoft Cardspace and extensions for other browsers, this login process will become even more integrated, as when a user is prompted for an OpenId and dialog will be displays asking the user to select the appropriate identity.
- Once users feel conformable using this method for wiki's and blogs, its only a matter of time before this will also expand to online shops and banking services.
Until recently there appeared no many major sites were willing to make the big step, however while investigating this Facebook launched OpenId integration within their site, so many be the flood gates are begining to open? see below article:
http://www.readwriteweb.com/archives/the_dam_just_broke_facebook_opens_up_to_openid.php
Within this project I looked at code samples to produce OpenID consumer applications for both Google Apps and .NET, however I didn't find one for Domino, so it may prove more difficult to implement on our existing infrastructure.
SHORT TERM BENEFITS
What immediate impact could the output of this R&D work have on the organisation – could it provide benefits without compromising our strategic approach?
Can not see any really short term benefits, however I believe this project has given use some useful insight into the direction of security and made clear that its something we should continue to monitor. In the medium/long term we should consider incorporating OpenId within our website, perhaps to start with using a similar method to the GovTrack site mentioned above. Although we would need to ensure we are fully happy with the security.
This would have benefits for both WCC and for public users:
- For WCC it would remove the overhead of password resets
- For the public with OpenId accounts it would make it easier to register as their information would be gathered from their OpenId provider, meaning they would not have to re-enter their standard details.
- Also as users have already verified their email address with their OpenId proivder this may remove to need for us to do this as well.
STRATEGIC IMPLICATIONS
How the work carried out fits with our strategic direction or how it should contribute to our strategic thinking.
I believe Identity 2.0 is something we should be keeping our eye on as this will probably become main stream within a few years. Authentication as a service would definately contribute to our strategic thinging. However with our current infrastructure and a lack of banks and government organisations currently using this method of authentication it might be wise not to become a too earlier adopter.
OTHER NOTES ETC
Dick Hardt – Presentation on Identity 2.0
http://www.youtube.com/watch?v=RrpajcAgR1E
Why OpenID leads to Information Cards
http://www.identityblog.com/wp-content/images/2008/02/OpenID/Normal/OpenIDPhish.html
The Python source code used to provide the Goggle Apps consumer app example shown above
http://code.google.com/p/google-app-engine-samples/downloads/detail?name=openid-consumer_20090125.tar.gz&can=2&q
The C# library used to provide the .NET consumer app example shown above
http://code.google.com/p/dotnetopenid/









